Where winit.exe came from
Winit.exe (Windows Initialize) was made by Microsoft and is a core system process that originated in Windows XP since it has been passed down to both Windows 7 and Vista. The file was created to allow uninstallers to run and process commands stored in the file WinInit.ini. This allows programs to take action while the computer is still booting up. In Windows 7 and Vista, it primarily acts as a launcher for the majority of the background applications that are always running. The file is stored locally on your computer at: If you find this executable stored in any other location, it is likely a virus that is disguising itself by using wininit.exe as its file name.
Should I disable wininit.exe?
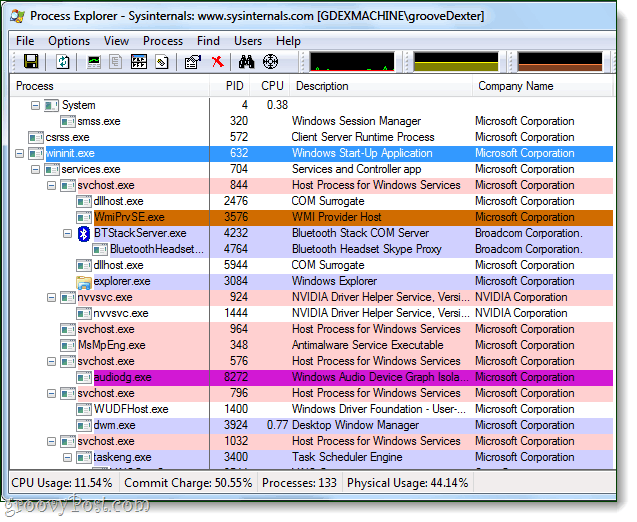
No, wininit.exe is a critical system process the Windows requires in order to function. Ending this process will likely result in a critical system error in which you’ll need to restart your computer. As you can see in the chart below, wininit.exe is at the top of the process tree for all of windows services, including svchost.exe.
Is wininit.exe dangerous?
On a brand new computer, wininit.exe doesn’t pose any threat at all. However on older computers that have been in use for while there is the potential problem of a virus renaming itself to wininit.exe in the form of a malicious copycat disguise. You should be fine though, as long as you have decent security software installed such as Microsoft Security Essentials.
Conclusion
Wininit.exe is a safe Windows executable that was put in place by Microsoft. By itself, the program is not malicious. The only danger is that the name can be copied by other programs in an attempt to mask the real virus, however, that can be said for nearly all programs. Yesterday it was at c:\documents and settings\oldeink\application data\wininit.exe Doing a restore got rid of it in the application data but it certainly is not at system32 It is more than likely a virus, be careful. Two of them involved wininit.exe. I guess I have two questions – are listening ports open ports and a security risk? If so, wouldn’t it be stupid to make wininit.exe accessible this way considering it is one of the most important applications in windows? Here is an example, one of two involving wininit on my computer right now in listening” state: Process: wininit.exe PID: 564 Protocol : TCP local address: (my computer) local port: 49152 Remote Address: (my computer) Remote Port: 0 State: LISTENING Comment Name * Email *
Δ Save my name and email and send me emails as new comments are made to this post.
![]()